Interactive Defense
Game

Instructions
Your Mission
Your firm has been contracted to defend the computer network of a major company at one of their manufacturing plants.
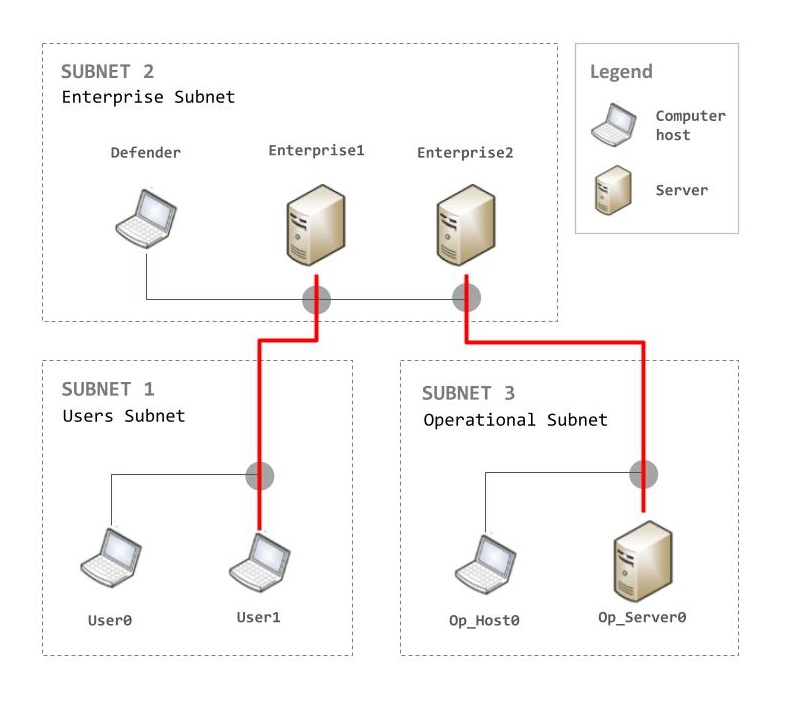
Attackers will be trying to get access to the Operational Server to steal the plans and disrupt the production. The easiest way for them to do so is to enter the network through one of the staff computers (User Hosts in Subnet 1) and progressively make their way up to the critical Operational Server (Op_Server0) in Subnet 3.
Each host or server on which an attacker got administrator-level access costs you some points.
To defend the network you will have to choose between one of these 4 actions:
- Monitor: letting the network activity occur without intervening - wait and see.
- Analyze: you can use this command to determine the exact access level of the attacker (User or Administrator level) on a specific host.
- Remove: if you think a host is being attacked, you can use this command to remove the attacker from this host.
- Restore: it restores the selected system (host or server) to a previous known good state. This has significant consequences for system availability, thus, it comes with a cost of -1 for you.
Scoring:
Each time, and as long as the attacker maintains administrator access on a host, you will keep losing a certain amount of points, reflecting the state of the system (the closer to 0, the more “healthy” the system is).If they reach the Operational Server (Op_Server0), the attackers will run an IMPACT attack costing you 10 points. Here is a summary of the cost of actions:
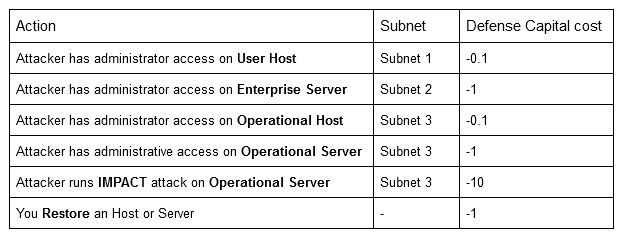
Your goal, as a security expert, is to minimize your loss by blocking the attacker’s intrusion into the network.
- Each episode is a fixed number of 25 rounds. You have to defend the network until the end of the 25 rounds.
- Each turn, you will have to decide which action is the best suited to defend the network according to the current state observed
You can watch this introduction video for an example.